GATE Technology
GATE technology provides interception-resistant authentication and encryption system. The principle of GATE technology is to use deception and ambiguity against the would be hacker, by masking password characters within groups.�
For the simplest of examples, say your password character is the letter ‘A’:
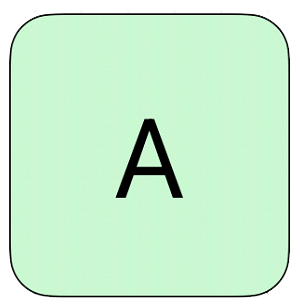
Now imagine that the key of the keypad is presented as a group of four characters, such as ‘A’, ‘B’, ‘C’ and ‘D’:
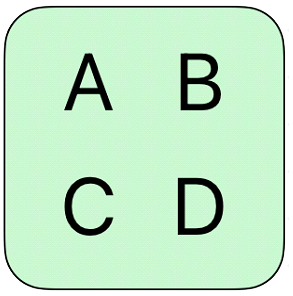
When that key is selected by you then the hacker does not know which of the four presented characters is yours.�
Therefore, even if they see you select that key, when they hope to use your password to pretend to be you, and they are presented with a key such as ‘X’, ‘Y’, ‘$’ and ‘A’, they do not know whether to select it:
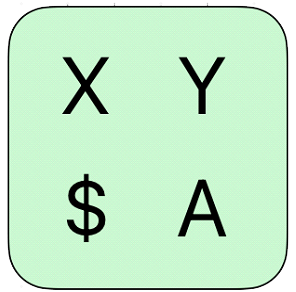
Of course the implementation of GATE technology is not as simple as this, where the algorithms being applied to make these concepts practical for the user and impossible for the hacker are continually evolving.�
Basic implementation choices of password complexity would include the following:
⦁ character choice: letters, numbers, special characters, foreign characters, images, emojis and so on
⦁ password length and dictionary rules
⦁ number of characters per key
⦁ keypad dimensions (or keypad rendering per key selection)
⦁ GATE locations – where to site access and permission levels within an environment
For example, a simple four character password might be:
| B | H | 8 | 🔥 |
|---|
An interesting three by three keypad rendering might be:
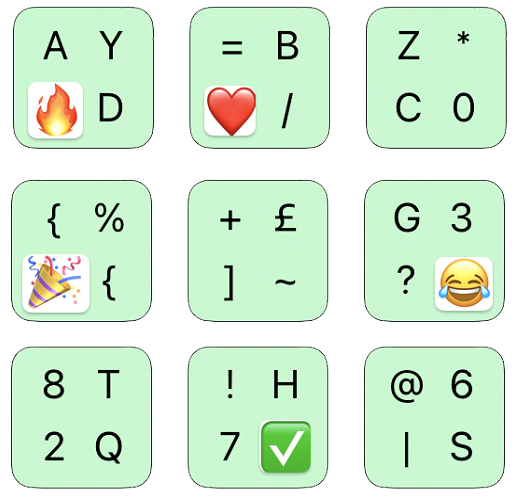
When you enter your password, the hacker, whether looking over your shoulder, logging your finger positions, or intercepting the key press communications, cannot possible know your password.
Clearly one of the most important questions in any implementation of GATE regards how secure the user wishes their data/access to be – in effect how many times they would require a hacker to observe/intercept their password entry before being able to decipher what the password actually is. Hand in hand with addressing this question in implementation, is how often a user will be content to change their password in order to stay ahead of the hacker and how many failed attempts they are willing to accept in implementation security rules. The answers to these questions, along with the GATE policy options, yield to a huge range of implementation choices for I AM GATE to consult and help our clients with in order to arrive at the perfect solution for their customers and server to server communication security.
One particularly useful feature of the GATE concept is to use Dummy characters in rendering keypads. This feature in GATE algorithms allows keypads to be rendered where one of more of the user’s password characters may be entirely missing from the keypad. In such a case, the user can select any key in place of selecting the missing character. This policy exponentially confuses the would-be hacker and can put his interception requirement beyond the possible.
